Re: [EXT] Re: [E] Re: k8s deployment - too many redirects - Mailing list pgadmin-support
| From | Yogesh Mahajan |
|---|---|
| Subject | Re: [EXT] Re: [E] Re: k8s deployment - too many redirects |
| Date | |
| Msg-id | CAMa=N=ONiq=WMASSgYu9hqaFVHfEZAMFduxU8d9q-v4smhV0kQ@mail.gmail.com Whole thread Raw |
| In response to | k8s deployment - too many redirects ("Schroeder, Steven" <steven.schroeder@verizonwireless.com>) |
| List | pgadmin-support |
ENHANCED_COOKIE_PROTECTION enables pgadmin to create session cookies based on IP address. As kubernetes uses dynamic ip address hosting, this is required to set False.COOL
can you pls share some technical background about
PGADMIN_CONFIG_ENHANCED_COOKIE_PROTECTION
was not aware about that one till today ..Thx & cheers
Heiko
From: "Schroeder, Steven" <steven.schroeder@verizonwireless.com>
Date: Monday, 16. May 2022 at 15:54
To: Yogesh Mahajan <yogesh.mahajan@enterprisedb.com>
Cc: pgAdmin Support <pgadmin-support@postgresql.org>
Subject: [EXT] Re: [E] Re: k8s deployment - too many redirects
Well, after adding 'PGADMIN_CONFIG_ENHANCED_COOKIE_PROTECTION = "False"' I am able to login via chrome now!!
On Mon, May 16, 2022 at 9:08 AM Yogesh Mahajan <yogesh.mahajan@enterprisedb.com> wrote:
Hi,
Can you please try setting the environment variable values below while spinning up pgadmin.
PGADMIN_CONFIG_ENHANCED_COOKIE_PROTECTION = False
PGADMIN_CONFIG_CONSOLE_LOG_LEVEL=10'
Thanks,
Yogesh Mahajan
EnterpriseDB
On Mon, May 16, 2022 at 5:31 PM Schroeder, Steven <steven.schroeder@verizonwireless.com> wrote:
Hi,
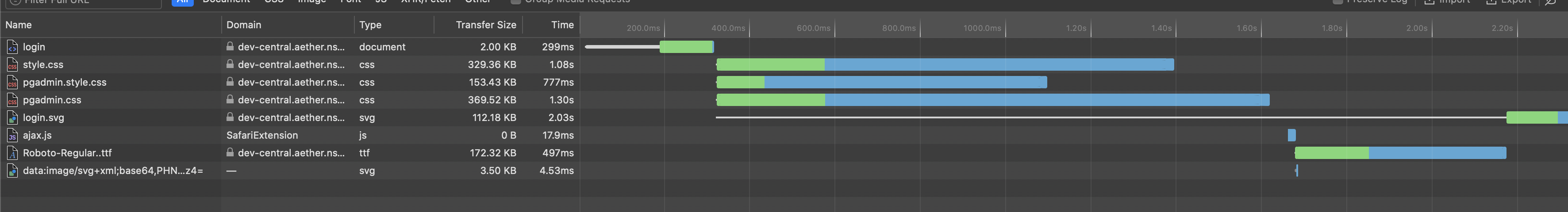
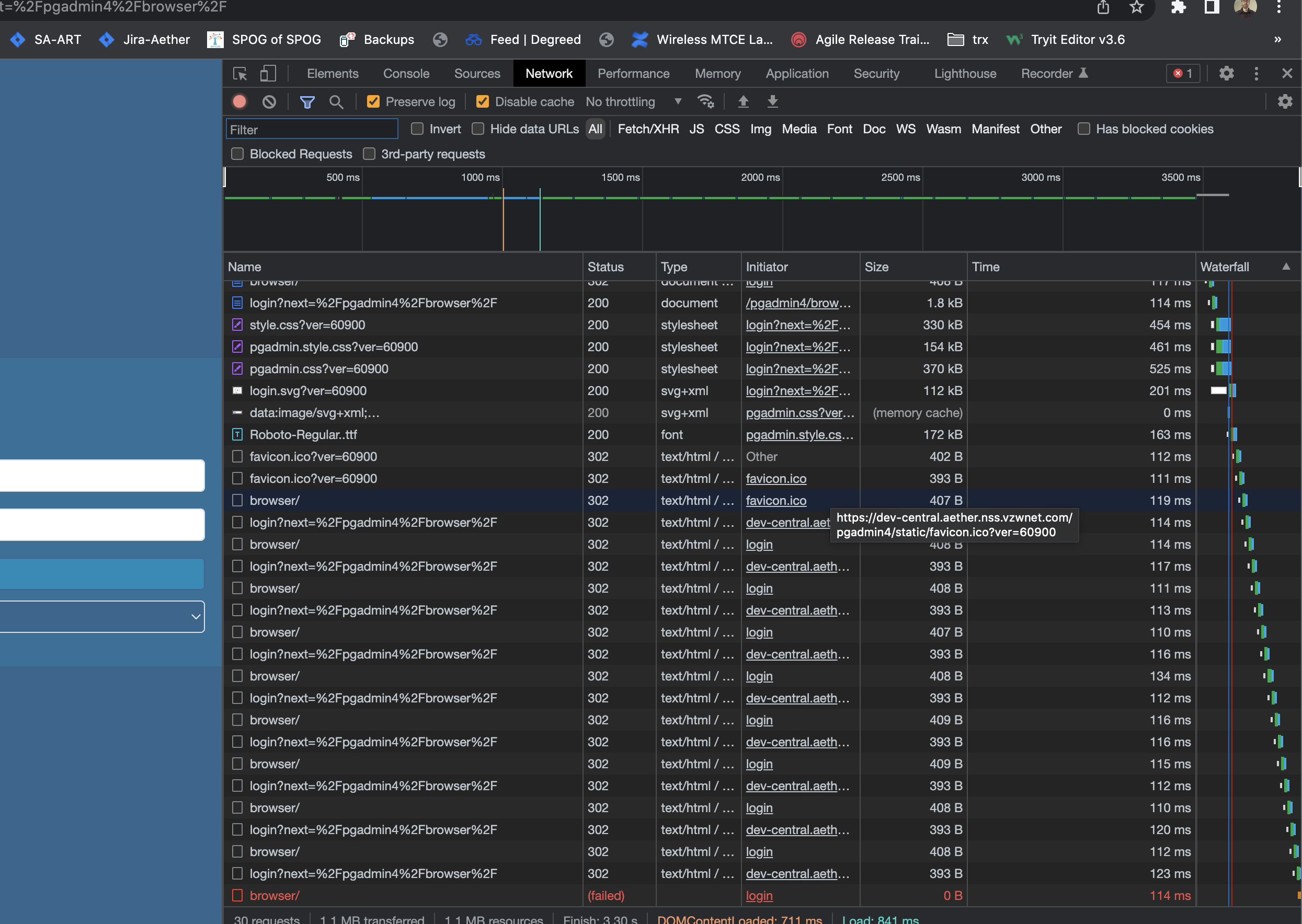
Was wondering if you had any possible suggestions as to why I am seeing the redirect from pgadmin only when using chrome. Below is a tcpdump running with the 302 being returned from the container.
I have seen others complain of the same issue, but never saw anyone had a resolution.
14:37:42.921775 IP (tos 0x0, ttl 64, id 33888, offset 0, flags [DF], proto TCP (6), length 1135)
192.168.162.64.45744 > 192.168.210.141.webcache: Flags [P.], cksum 0x8976 (correct), seq 24521:25604, ack 20533, win 1186, options [nop,nop,TS val 189067388 ecr 448904947], length 1083: HTTP, length: 1083
GET /pgadmin4/browser/ HTTP/1.1
Host: dev-central.xxx.nss.xxx.com
X-Request-ID: 8ae64bf0c6e42bad3925ddb3d25fd882
X-Real-IP: 10.133.48.140
X-Forwarded-For: 10.133.48.140
X-Forwarded-Host: dev-central.xxx.nss.xxx.com
X-Forwarded-Port: 443
X-Forwarded-Proto: https
X-Forwarded-Scheme: https
X-Scheme: https
X-Script-Name: /pgadmin4
sec-ch-ua: " Not A;Brand";v="99", "Chromium";v="101", "Google Chrome";v="101"
sec-ch-ua-mobile: ?0
user-agent: Mozilla/5.0 (Macintosh; Intel Mac OS X 10_15_7) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/101.0.4951.64 Safari/537.36 VZWEDN VZWEDN VZWEDN VZWEDN VZWEDN VZWEDN VZWEDN VZWEDN VZWEDN VZWEDN VZWEDN VZWEDN VZWEDN VZWEDN VZWEDN VZWEDN VZWEDN VZWEDN VZWEDN VZWEDN VZWEDN
sec-ch-ua-platform: "macOS"
accept: image/avif,image/webp,image/apng,image/svg+xml,image/*,*/*;q=0.8
sec-fetch-site: same-origin
sec-fetch-mode: no-cors
sec-fetch-dest: image
referer: https://dev-central.xxx.nss.xxx.com/pgadmin4/login?next=%2Fpgadmin4%2Fbrowser%2F
accept-encoding: gzip, deflate, br
accept-language: en-US,en;q=0.9
14:37:42.924528 IP (tos 0x0, ttl 63, id 30390, offset 0, flags [DF], proto TCP (6), length 643)
192.168.210.141.webcache > 192.168.162.64.45744: Flags [P.], cksum 0xf894 (incorrect -> 0xabd7), seq 20533:21124, ack 25604, win 679, options [nop,nop,TS val 448905049 ecr 189067388], length 591: HTTP, length: 591
HTTP/1.1 302 FOUND
Server: gunicorn
Date: Sat, 14 May 2022 18:37:42 GMT
Connection: keep-alive
Content-Type: text/html; charset=utf-8
Content-Length: 296
Location: /pgadmin4/login?next=%2Fpgadmin4%2Fbrowser%2F
Vary: Accept-Encoding
X-Frame-Options: SAMEORIGIN
Content-Security-Policy: default-src ws: http: data: blob: 'unsafe-inline' 'unsafe-eval';
X-Content-Type-Options: nosniff
X-XSS-Protection: 1; mode=block
Set-Cookie: pga4_session=3c94be8e-e8cc-4a48-ba64-46519fe16f24!Xspu3VIKd1VpDNtTacr+vzaDiJY=; Expires=Sun, 15 May 2022 18:37:42 GMT; HttpOnly; Path=/; SameSite=Lax
On Thu, May 12, 2022 at 7:21 PM Schroeder, Steven <steven.schroeder@verizonwireless.com> wrote:
If I keep trying to log in using chrome, it eventually takes the password, but just sits there loading...
From the container logs:
2022-05-12 23:13:48,919: DEBUG pgadmin: Authentication initiated via source: ldap
98
2022-05-12 23:13:50,888: DEBUG pgadmin: Authentication and Login successfully done via source : ldap
From Browser:
On Thu, May 12, 2022 at 6:36 PM Schroeder, Steven <steven.schroeder@verizonwireless.com> wrote:
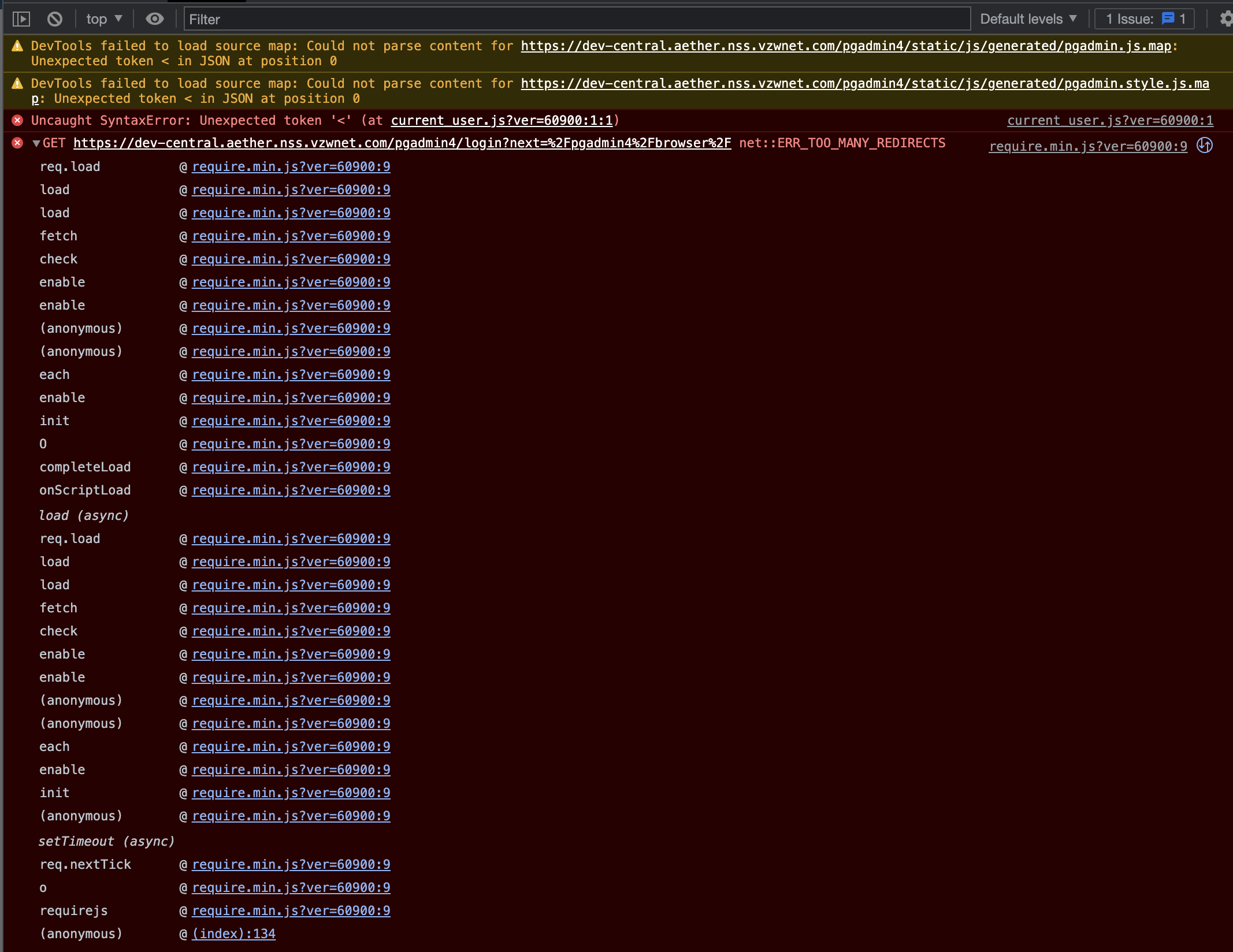
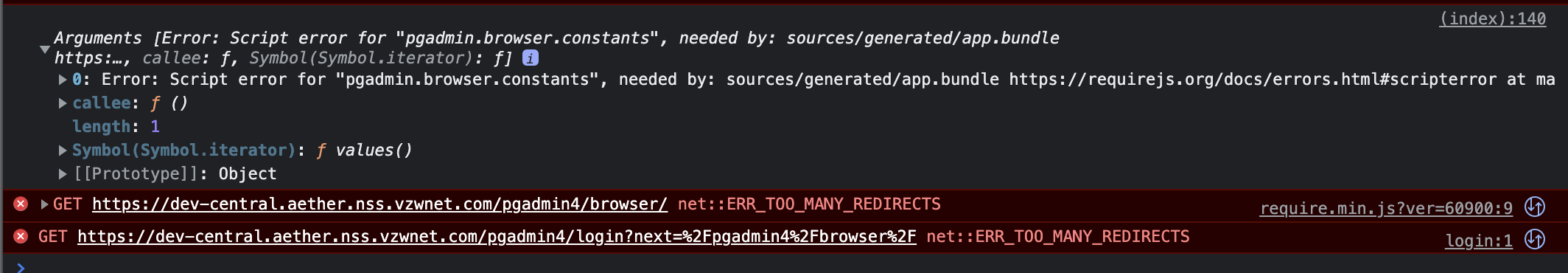
It seems that only chrome is displaying the 302 redirects, safari is not. I have tried everything possible, but I can't figure it out.
This is from safari:
This is from chrome. The login page loads, but you can't log in except when in incognito. I can't figure out for the life of me why chrome shows the redirects, but safari doesn't.
On Thu, May 12, 2022 at 6:55 AM Schroeder, Steven <steven.schroeder@verizonwireless.com> wrote:
Yep, I definitely cleared my cache several times with the same results. I have deployed pgadmin in 2 separate k8s environments as well with the exact same results.
I do not have any other session going. The weird thing is another employee using a windows pc on chrome works fine. I am using chrome on a mac.
On Thu, May 12, 2022 at 12:56 AM Yogesh Mahajan <yogesh.mahajan@enterprisedb.com> wrote:
Hi Steven,
Can you please try clearing cache in chrome browser? or Is there an already existing session with LDAP credentials in chrome?
Incognito mode launches with NO cache, hence pgAdmin is working fine in incognito mode.
Thanks,
Yogesh Mahajan
EnterpriseDB
On Wed, May 11, 2022 at 4:53 PM Schroeder, Steven <steven.schroeder@verizonwireless.com> wrote:
Hey All,
I recently got pgadmin somewhat working when running in k8s. I am now facing an issue where I can login via ldap on chrome, but only in incognito mode.
When not in incognito mode, I am seeing 'too many redirects' which seems to be affecting login. It does work okay when using safari.
Is there any way to eliminate the 'too many redirects'? Below is my k8s ingress for this deployment.
apiVersion: networking.k8s.io/v1
kind: Ingress
metadata:
name: ict-pgadmin
namespace: gq2v
annotations:
kubernetes.io/ingress.class: nginx
nginx.ingress.kubernetes.io/proxy-buffer-size: "32k"
nginx.ingress.kubernetes.io/proxy-body-size: 8m
nginx.ingress.kubernetes.io/configuration-snippet: |
proxy_set_header X-Script-Name "/pgadmin";
spec:
rules:
- host: dev-central.aether.nss.vzwnet.com
http:
paths:
- path: /pgadmin
pathType: Prefix
backend:
service:
name: ict-pgadmin-svc
port:
number: 8080
Thanks,
Steve
--
Steve Schroeder | verizon
Service Assurance
O 908-203-5487 | M 609-226-5995
--
Steve Schroeder | verizon
Service Assurance
O 908-203-5487 | M 609-226-5995
--
Steve Schroeder | verizon
Service Assurance
O 908-203-5487 | M 609-226-5995
--
Steve Schroeder | verizon
Service Assurance
O 908-203-5487 | M 609-226-5995
--
Steve Schroeder | verizon
Service Assurance
O 908-203-5487 | M 609-226-5995
Geschäftsanschrift/Business address: Wipro Business Solutions GmbH, Metro-Straße 12, 40235 Duesseldorf, Germany
Geschäftsführung/Management Board: Thomas Viefhaus, Michael Seiger, Anandh RaghavanSitz Düsseldorf, Amtsgericht Düsseldorf, HRB 18232/Registered Office Düsseldorf, Commercial Register of the Düsseldorf Local Court, HRB 18232
Betreffend Mails von *@metroitpartner.com
Die in dieser E-Mail enthaltenen Nachrichten und Anhänge sind ausschließlich für den bezeichneten Adressaten bestimmt. Sie können rechtlich geschützte, vertrauliche Informationen enthalten. Falls Sie nicht der bezeichnete Empfänger oder zum Empfang dieser E-Mail nicht berechtigt sind, ist die Verwendung, Vervielfältigung oder Weitergabe der Nachrichten und Anhänge untersagt. Falls Sie diese E-Mail irrtümlich erhalten haben, informieren Sie bitte unverzüglich den Absender und vernichten Sie die E-Mail.Regarding mails from *@metroitpartner.com
This e-mail message and any attachment are intended exclusively for the named addressee. They may contain confidential information which may also be protected by professional secrecy. Unless you are the named addressee (or authorised to receive for the addressee) you may not copy or use this message or any attachment or disclose the contents to anyone else. If this e-mail was
Attachment
pgadmin-support by date: